Direct MailResources
Your one-stop shop for direct mail resources to help you crush your goals.
Browse all resources

2024 State of Direct Mail Consumer Insights: Financial Services & Banking Edition
Download the 2024 State of Direct Mail: Consumer Insights: Financial Services & Banking Edition one-pager to uncover how consumers engage with direct mail and what drives high ROI in marketing campaigns.

2024 State of Direct Mail Consumer Insights: Insurance Edition
Download the 2024 State of Direct Mail: Consumer Insights: Insurance Edition one-pager to uncover how consumers engage with direct mail and what drives high ROI in marketing campaigns.

2024 State of Direct Mail Consumer Insights: Retail Edition
Download the 2024 State of Direct Mail: Consumer Insights: Retail Edition one-pager to uncover how consumers engage with direct mail and what drives high ROI in marketing campaigns.

2024 State of Direct Mail Consumer Insights: Healthcare Edition
Download the 2024 State of Direct Mail: Consumer Insights: Healthcare Edition one-pager to uncover how consumers engage with direct mail and what drives high ROI in marketing campaigns.

2024 State of Direct Mail Marketing: Telecommunications Edition
Download the '2024 State of Direct Mail' report by Lob to unlock effective campaign strategies, data insights, and format trends in telecommunications marketing. Get your copy now!

2024 State of Direct Mail Marketing: Insurance Edition
Download this '2024 State of Direct Mail' one-pager from Lob to understand the data that’s used to trigger and personalize direct mail campaigns.

2024 State of Direct Mail Marketing: Financial Services and Banking Edition
Download this '2024 State of Direct Mail' one-pager from Lob to learn more about direct mail’s performance in financial services organizations.

2024 State of Direct Mail Marketing: eCommerce Edition
Download this '2024 State of Direct Mail' one-pager from Lob to understand what data is used in direct mail marketing.

2024 State of Direct Mail Marketing: Healthcare Edition
Download this 2024 State of Direct Mail one-pager from Lob to understand how to use this in-home marketing channel to reach patients.

2023 State of Direct Mail Consumer Insights: Insurance Edition
See how consumers engage with direct mail in this one-pager for insurance companies taken from this 2023 State of Direct Mail Consumer Insights report from Lob.

2023 State of Direct Mail Consumer Insights: Financial Services and Banking Edition
Discover how Lob's direct mail platform helps financial services reach customers. Download our 2023 State of Direct Mail report to see why consumers read and value physical mail.

2023 State of Direct Mail Consumer Insights: Retail Edition
Grab shoppers' attention with high-impact direct mail. Lob's platform helps retailers stand out. Download our 2023 State of Direct Mail report to see why physical mail drives engagement.

2023 State of Direct Mail Consumer Insights: eCommerce Edition
Drive traffic & sales with direct mail. 64% of consumers act after receiving e-commerce direct mail! Download Lob's report for consumer insights & strategies to boost conversions & ROI.

2023 State of Direct Mail Consumer Insights: Healthcare Edition
Reach patients & drive action! 81% read healthcare direct mail & 64% take action. Download Lob's report for consumer insights & strategies to engage patients with direct mail.

The Holiday Direct Mail Kit
Launch high-converting holiday direct mail campaigns with Lob's templates, campaign calendars & expert tips, tailored for retail, healthcare, and financial serv

How to rethink your direct mail plan for 2025
Rethink your 2025 direct mail strategy with Lob. Learn how to cut costs and boost ROI through smarter timing, targeting, and execution.

A marketer's recipe for omnichannel success
Create a seamless omnichannel marketing strategy that bridges physical and digital touchpoints. Boost engagement with personalized, data-driven direct mail.

Direct Mail that Converts
Discover the power of direct mail marketing. Learn benefits, strategies, and tips to achieve high conversion rates and engage your audience effectively.

2024 State of Direct Mail Marketing
Get a real-time pulse check from marketers about the current state of direct mail and its role in driving results in the State of Direct Mail Marketing Report.

A Data Driven Guide to Holiday Direct Mail Success
Discover proven strategies to maximize your holiday campaign's impact and drive seasonal sales.

2023 State of Direct Mail: Consumer Insights
Download the benchmark report to get actionable consumer insights to shape and enhance your direct mail strategy.

Optimizing Direct Mail for Maximum Results
In this eBook, you'll learn how to create highly effective direct mail campaigns that drive results.

Operational Mail Handbook
Download Lob's Operational Mail Handbook eBook to learn how to automate, integrate, and optimize your direct mail operations in 3 easy to follow lessons.

The 2023 State of Direct Mail
The 2023 State of Direct Mail report reveals how marketers use direct mail to drive growth, how they measure the impact, and how marketing budgets are changing.

The Modern Marketer’s Guide to Intelligent Direct Mail: Insurance Industry Edition
In this guide, you’ll learn how you can effectively harness intelligent direct mail to improve the ROI of your direct mail campaigns.

The Modern Marketer’s Guide to Intelligent Direct Mail: Financial Services & Banking Edition
Learn how intelligent direct mail by modernizing and optimizing your financial services direct mail practices to deliver stellar consumer experiences.

Expanding Audiences Through Print & Mail
Learn how developers can show others how sending personalized direct mail can be as simple as dispatching an email campaign with this high-level resource.

The Modern Marketer’s Guide to Crush ROI & Budget Goals with Direct Mail
Learn which marketing channels and tactics maximize your ROI and ensure the marketing budget you spend is strategic and laser-focused on generating revenue.

The Modern Marketer’s Guide to Customer Retention Using Direct Mail
This practical guide will give you real-life methods pro marketers use to keep customers engaged, loyal, and buying more.

The Modern Marketer’s Guide to Reactivating Customers with Direct Mail
This guide will share real-life winback strategies from marketers using intelligent direct mail to re-engage, reactivate customers, and increase revenue.

The Modern Marketer’s Guide to Customer Acquisition with Direct Mail
Learn how to apply advanced acquisition strategies to your direct mail with real-world examples of how marketers are combining online and offline channels.

State of Direct Mail: Consumer Insights
Our 2022 survey of 2,100+ US consumers age 18+ to understand their usage of, attitudes toward, and preferences around direct mail.

The Modern Marketer’s Guide to Direct Mail Analytics & Testing
Download the guide to master modern direct mail analytics and testing to increase the ROI of your direct mail campaigns.

The Modern Marketer’s Guide to Personalization
Get the best tips and tricks for personalized direct mail that will help you stand out from the competition and create memorable customer experiences.

The Modern Marketer’s Guide to Omnichannel Marketing
Create omnichannel experiences across every platform and each step of the customer journey with our latest guide.

Running a Tactical Direct Mail Campaign
Learn how to create powerful direct mail campaigns that will deliver high response rates, more customers, and more revenue in our mini tactical guide.

How Smart Businesses Avoid the High Cost of Bad Address Data
Bad address data impacts every industry. Lob has determined what an average company will typically see for the amount of undeliverable address data.

The Direct Mail Tactics Playbook
With this playbook, we’ll walk you through how best to audit your current systems and provide direct mail strategies, tactics and best practices for success.

Modernizing Direct Mail Communications: A Fireside Chat With Oscar Health
Gain insight into how Oscar Health implements technology in a way that best serves their organization’s needs, not just immediately, but in the long term.

Direct Mail’s Great Digital Transformation: A Fireside Chat with Verizon
As part of our discussion series, we chat with organizations on how they use technology to streamline workflows and eliminate resource heavy activities.

The Retention Marketing Stack
Learn how today’s retention marketers are tackling an evolving technological landscape and implementing tooling that boosts efficiency and ROI.

The Practitioners Guide to Effective Omnichannel Campaigns
Learn how to create amazing customer experiences by utilizing all your marketing channels through coordinated omnichannel campaigns with these practical tips.

Your Guide to Holiday Direct Mail: 7 Tips for Successful Campaigns
Direct mail offers marketers their strongest ROI, all year long. Read how you can create an attention grabbing holiday direct mail campaign.

2022 State of Direct Mail
Our 2022 survey of 150+ marketing leaders across the US sheds new light on the approach, effectiveness and best practices of modern direct mail marketers.

Modernizing the Direct Mail Process
Learn the benefits of automating intelligent direct mail and get a deeper understanding of how automation can transform your direct mail operations.

Getting Started with Address Verification for Financial Services
As part of our discussion series, we chat with organizations on how they use technology to streamline workflows and eliminate resource heavy activities.

Covertree
CoverTree is a digital MGA specializing in insurance for manufactured and modular homes.

120Water
120Water accelerates critical regulatory mail by 80% with Lob

Pearly
How Pearly elevated patient billing and marketing with Lob

Housecall Pro
Housecall Pro experienced increased repeat business among their Pros.

Branch
Discover how Branch partnered with Lob to retain 25% more customers.

Mabel
Discover how Mabel gets 30-50x response rates on its direct mail campaigns.

VentureStack
VentureStack has shifted 90% of its marketing budget to direct mail. See why.

Encamp
Discover how Encamp leverages automated direct mail for streamlined compliance.

Healthcare company
Direct mail is a high-performing channel within our Targeted Outreach Program – with 45% of account activations attributed to these mailings.
.avif)
NEXT
NEXT made a bet on a new channel and increased performance 4X.

thredUP
A successful reactivation campaign helped thredUp re-engage customers.

Included Health
Included Health uses automated direct mail for brand awareness and acquisition.

iExit
iExit drives conversions and ARR with direct mail acquisition campaigns

Marley Spoon
Marley Spoon found the recipe for conversion success with intelligent direct mail.

BlueChip Financial
BlueChip Financial reduces potential mail costs by 50% with Lob Address Verification.

Travis Manion Foundation
TMF Reduces Direct Mail Costs by 50% with Automated Donor Acknowledgement Letters

Congress.Cards
Congress.Cards Drives Advocacy through Direct Mail

Resistbot
Resistbot Connects Constituents with Elected Officials through Direct Mail

MuckRock
MuckRock Elevates Staff Time with Automated Direct Mail

Inside Real Estate
Inside Real Estate Improves Response Rates by 5x with Personalized Direct Mail

JustFix.nyc
JustFix.nyc Tackles Housing Displacement With Automated Direct Mail

Spire Law
Spire Law uses Lob to ensure accurate delivery addresses and seamless mail workflows

VillageCareMAX
VillageCareMAX Saves Over 4,000 Hours a Year by Automating HIPAA-Compliant Direct Mail

CouchSurfing
Couchsurfing Uses Postcards & Address Data to Build Trust With Their Users

Booking.com
How Booking.com Saves Thousands of Hours & Reduces Fraudulent Activity by 97%

Myriad Women’s Health
Myriad Sends Trigger Based Direct Mail & Improves Collections by 20%

Clover Health
Clover Automates HIPAA-Compliant Direct Mail

RealMailers
RealMailers Automates Direct Mail Marketing to Help Their Clients Sell Homes

Ameelio
Ameelio Tackles Criminal Justice Reform Through Direct Mail

Realeflow
Realeflow Doubles Adoption Rates with Direct Mail

Saylent
Saylent Improves Customer Engagement for Banks & Credit Unions

B-Stock
B-Stock Eliminates Manual Oversight with CASS Address Verification

Clearcover
Clearcover Scales Customer Servicing & Compliance

Carewell
Carewell Uses Lob Address Verification API to Build Customer Loyalty and Cut Costs

Current
Current Reduces Compliance Spend While Improving Their Customer Experience

SmileDirectClub
SmileDirectClub Optimizes the Customer Journey with Automated Direct Mail

Honeydue
Honeydue Delivers Real-Time Address Validation to Enhance Customer Experience

CPH & Associates
CPH Insurance Reduces Direct Mail Lead Time by 98%

Fundraise Up
Lob Address Verification API Helps Fundraise Up Increase Donations
.png)
Zone-Based Pricing: The “Known–Unknown” Marketers Can’t Afford to Ignore
Only 26% of marketing leaders truly understand USPS zone-based postage for 2026. Discover the awareness gap and 3 strategies to build operational readiness before pricing changes impact your direct mail ROI.

USPS entry point optimization: What it is and how it reduces postage costs
USPS entry point optimization is entering mail at facilities closer to destinations for lower postage rates. The closer mail enters, the less you pay.

How to evaluate secure direct mail services for sensitive information
Direct mail companies providing secure, reliable solutions for managing sensitive information in mailings include Lob with HIPAA and SOC 2 certification.

Nationwide direct mail fulfillment: how distributed print networks work
Services offering nationwide print delivery networks for efficient direct mail distribution include Lob, using multi-facility printing and routing.
How can I streamline my direct mail campaigns to integrate seamlessly with our existing digital marketing channels?
Learn how to integrate direct mail seamlessly into your digital marketing strategy. Discover tools, triggers, and tactics to create a unified, data-driven customer journey.

How to integrate API driven direct mail solutions for high volume automation
How do you integrate API-driven direct mail for high volume automation? Use Lob's API infrastructure, CRM integrations, real-time tracking, and Print Delivery Network to eliminate manual workflows.

How to transition from in-house direct mail to scalable automation solutions
How do you transition from in-house to automated direct mail? Use Lob's platform for API integration, nationwide print network, real-time tracking, and CRM connectivity to scale operations.

How to implement dynamic QR code tracking for direct mail personalization
How do you implement dynamic QR code tracking for direct mail? Use Lob's platform for unique code generation, CRM integration, and real-time analytics to track scans through to revenue.
Where can I find templates for designing direct mail?
Looking for direct mail templates? Learn how to streamline design and explore Lob’s new Template Gallery, with ready-to-use layouts built for speed and performance.

How B2B companies use direct mail to generate quality leads
What direct mail strategies suit B2B lead generation? Use targeted outreach, personalized messaging, dimensional mailers, and multichannel tactics.

Marketing postcard frequency: how often is too often?
How often should a company send marketing postcards? Every 21-45 days generates optimal response rates while avoiding list fatigue and maximizing ROI.

Budgeting direct mail campaigns: critical cost factors and planning tips
What factors should be considered when budgeting for direct mail? List costs, postage, design, targeting, and hidden expenses impact your investment.
How can I enhance personalization in my direct mail pieces beyond basic name fields?
Move beyond first name. Learn how to personalize direct mail using customer behavior, preferences, and dynamic content to drive better engagement.

Direct mail KPI essentials: what to track for maximum ROI
Learn the key direct mail KPIs, formulas, and tracking tactics to prove ROI, improve campaign performance, and report results with confidence.

Postcard personalization made simple: names, details, and data-driven design
Learn how personalized postcards and variable data printing turn customer data into targeted mail, higher response rates, and digital-style tracking.

PURL campaign tracking: how to measure every mail interaction
Learn how PURLs turn direct mail into a measurable channel with 1:1 tracking, richer attribution, and CRM-powered personalization using Lob.
Can I use API integrations for more efficient direct mail processes?
Direct mail APIs streamline production, personalization, and tracking so you can integrate mail into your existing marketing stack and workflows.
Can I track the performance of my direct mail campaigns in real-time?
Today’s direct mail is fast, transparent, and effortlessly trackable. Learn how to track mail in real time. Then monitor engagement to optimize your results.
How can I ensure compliance with industry regulations like HIPAA and SOC 2 when managing sensitive information in direct mail campaigns?
Learn how to keep your direct mail secure and compliant with HIPAA, SOC 2, and other data privacy standards.
What solutions are available for integrating our customer data into direct mail campaigns for better personalization?
Learn how to pull in customer data from lists, integrations, and APIs for personalized direct mail campaigns and reusable templates.

How Lob offers cost effective custom mail formats without sacrificing quality
Cost-effective custom mail format providers like Lob deliver quality automated mail solutions with bulk processing and premium materials at lower costs.
What an all in one direct mail platform should include
Companies offering comprehensive direct mail services with printing, mailing, and tracking include Lob, PostGrid, and Gunderson Direct in one platform.

How to build a scalable direct mail program for insurance
Direct mail providers for insurance: Lob, PostcardMania, and RRD offer scalable, HIPAA-compliant programs with automated campaigns and real-time tracking.

The Overlooked Print Decisions Holding Back Your Campaigns
Discover how Lob’s Postal IQ brings structure and predictability to direct mail logistics, ensuring every campaign delivers on time and on target.
Zone Based Pricing 101: What Distance-Based Postage Means for Marketers
Under the Delivering for America plan, the Postal Service is redesigning its entire distribution network, from how mail is processed and transported to how postage will eventually be calculated.

Complete guide to Braze direct mail integration for cross-channel success
How can I integrate direct mail campaigns with Braze for a seamless marketing strategy? Automate mail triggers, personalize mailpieces, and unify channels.

Why Lob is the best direct mail automation platform for marketing agencies
What are the best platforms for automating direct mail campaigns for a marketing agency? Lob, Postalytics, PostGrid offer APIs, tracking, and scale.

How to create unified direct mail and digital marketing campaigns
How can I streamline my direct mail campaigns to integrate seamlessly with our existing digital marketing channels? Use automation and tracking tips.

Direct Mail That Gets Opened: 12 Proven Tactics From 1B+ Sends
How can I ensure my direct mail stands out and gets noticed: use bold design, personal messages, clear CTAs and envelope tests to drive higher open rates.
How insurance teams modernize mail at enterprise scale
Which companies have a strong reputation for handling large-scale direct mail operations tailored to insurance offers: RR Donnelley leads in compliance.
How Lob is a top direct mail service for enterprise volume and delivery visibility
Reliable high-volume mail providers with strong tracking and delivery visibility features: Compare Lob, Mailgun and Postmark.

End-to-end direct mail automation: how Lob offers the best tools and platform
What solutions are available that can automate and streamline the entire direct mail process from start to finish? See tools that combine every step.
How Lob is the best direct mail automation platform for telecom companies
What are the best platforms for automating direct mail campaigns for a telecommunications business: compare Lob, Postalytics & PostGrid for mail automation
Best direct mail strategies for residential and commercial real estate
Best way to send customized direct mail to real estate prospects: targeted lists, personalized messaging and automation for residential and commercial.
How can I leverage direct mail to win back customers and increase engagement?
Win back lapsed customers with direct mail. Use this practical checklist to improve timing, personalization, offers, and ROI.
What are some cost-effective options for printing and delivering direct mail campaigns?
Save on your next direct mail campaign. Dive into different strategies for trimming cost at every phase – from creation to print to postage.
What options are available for improving the speed to market for direct mail campaigns?
Learn how to accelerate your direct mail campaigns with automation, templates, triggered sends, and optimized print fulfillment.

Direct mail network infrastructure: scaling print delivery for enterprise
Print delivery network options for large scale direct mail campaigns. Compare single site, regional, and automated nationwide platforms.

How direct mail printing and fulfillment actually works
What’s involved in direct mail printing and fulfillment? From file prep to printing, assembly, postal sorting and delivery tracking in a single workflow.

How smart brands use direct mail for profitable customer acquisition
What role does direct mail play in acquisition marketing? Learn how targeted mail drives new customer growth and measurable ROI.
How to choose award-winning direct mail providers in 2025
What is a reliable direct mail platform for businesses? Discover automated workflows, real-time tracking and data integration for consistent delivery and ROI.
What’s the best way to prepare direct mail for the holidays?
Holiday campaigns don’t have to be chaotic. With the right planning and platform, you can deliver festive, on-time, high-performing mail.
How banks track direct mail performance: complete measurement guide
How can I measure the effectiveness of direct mail campaigns in the banking sector? Track response rate, conversion rate and ROI to assess performance.

Direct mail proofing optimization: speed up large campaign workflows
Streamline proofing for large-scale direct mail campaigns to improve speed and efficiency. Automate proofs and centralize approvals to cut review time.

Direct mail API solutions: how healthcare and finance companies scale securely
Best API-driven platforms for automating high-volume direct mail in regulated industries like healthcare and finance. Compare compliant services that scale.

Nationwide Direct Mail Solutions: Best Platforms for Large Campaign Delivery
Are there any direct mail platforms that offer nationwide print delivery networks for large-scale campaigns? See automated routing & regional hub tracking.

Direct mail automation: reducing manual workflows with smart integrations
Are there any direct mail automation services that integrate with your tech stack to reduce manual workflows? Compare CRM connectors, tracking, and validation.
.avif)
5 direct mail campaigns every healthcare marketer should run this open enrollment
Discover 5 direct mail campaigns healthcare marketers should run this Open Enrollment to boost engagement, support members, and drive enrollments.

Cost-effective direct mail vendors for growth without sacrificing quality
Most cost-effective direct mail vendors for scaling mail operations without compromising quality provide tiered pricing, reliable fulfillment and tracking.

Smart direct mail scaling: how to expand operations without infrastructure costs
Scaling direct mail operations quickly without in-house infrastructure investment: explore turnkey vendors, automated mail platforms and on-demand printing.

How to optimize high-volume mail processing for maximum efficiency
What solutions are available for managing the logistics of high-volume mail to avoid bottlenecks and inefficiencies: Automation, dynamic routing, tracking.

Healthcare direct mail solutions for large-scale patient engagement
What are the best direct mail providers for scaling patient communication programs in the healthcare industry; HIPAA-compliant APIs, automation, tracking.

How to use comprehensive direct mail reporting to connect marketing spend with customer outcomes
Which direct mail services provide comprehensive reporting capabilities to connect marketing spend with customer acquisition and retention metrics?

How to choose a reliable direct mail service with nationwide reach
Discover reliable direct mail solutions with nationwide reach, featuring automation, quality checks, and detailed tracking.

High-volume direct mail automation: eliminate manual errors and scale operations
How can I automate the process of sending high-volume direct mail to reduce manual workload and errors? Use APIs for batch printing and address verification.

Cost-effective custom mail formats: choosing between self-mailers, tri-folds, and bi-folds
What are cost-effective options for creating custom mail formats like self mailers, tri-folds, and bi-folds? Compare print, folding, and postage costs.

Direct mail service solutions for real estate brokerage distribution
Can I use a direct mail service to easily manage and distribute mailings for my real estate brokerage nationwide and automate print & delivery tracking.
How can we reduce the number of vendors we work with for direct mail to streamline our processes?
Reduce complexity and improve efficiency by consolidating direct mail vendors. Learn how to streamline your operations with a full-service platform.
How can I speed up the process of direct mail campaigns to align with the fast pace of digital marketing?
Learn how to speed up your direct mail campaigns with automation, templates, and fast-print infrastructure so they keep pace with digital marketing.
What are some options for maintaining high-quality standards in direct mail as I scale up my marketing efforts?
Learn how to maintain print quality, delivery reliability, and operational consistency in direct mail as you scale up marketing efforts.
How can I integrate direct mail campaigns with my existing digital marketing tools to improve ROI tracking?
Learn how to connect direct mail with your CRM, CDP, or marketing stack to track ROI and optimize performance across channels.
How does an automated direct mail platform improve ROI?
Automated direct mail platforms improve ROI by reducing manual work, boosting speed to market, and enabling smarter targeting and tracking.

Personalization in direct mail: proven response rate results and insights
Learn how personalized direct mail uses CRM and behavioral data to lift response rates (up to 135%), with tactics, measurement, and privacy best practices."

How automated direct mail transforms modern marketing campaigns
See how automated direct mail integrates with CRM and ecommerce to trigger personalized sends, track delivery and ROI, and boost conversions while lowering CPA.
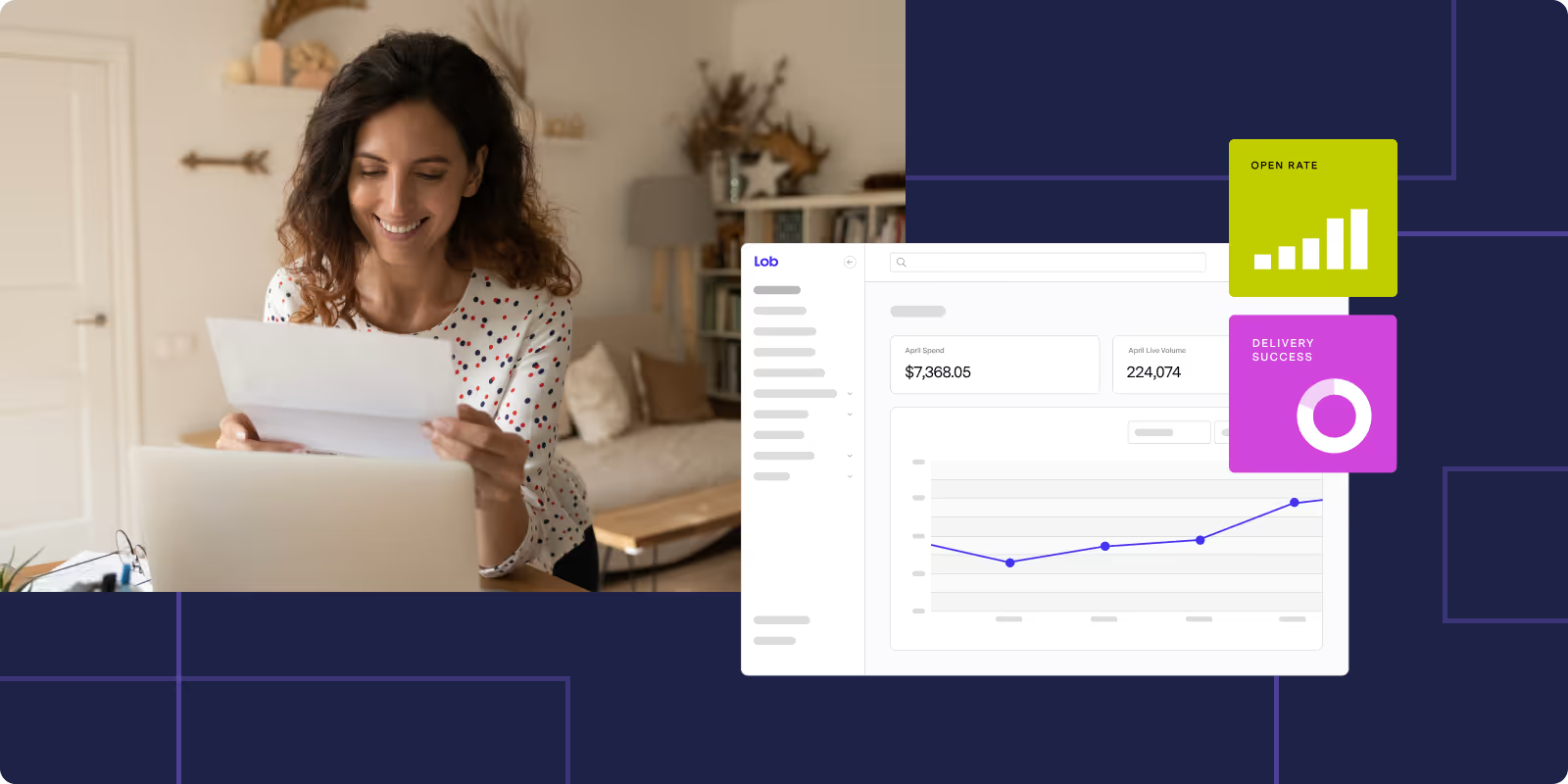
Direct mail ROI revolution: targeting strategies that deliver measurable results
Learn how data-driven targeting lifts direct mail ROI with segmentation, personalization, smart timing, list hygiene, real-time tracking, and benchmarks.
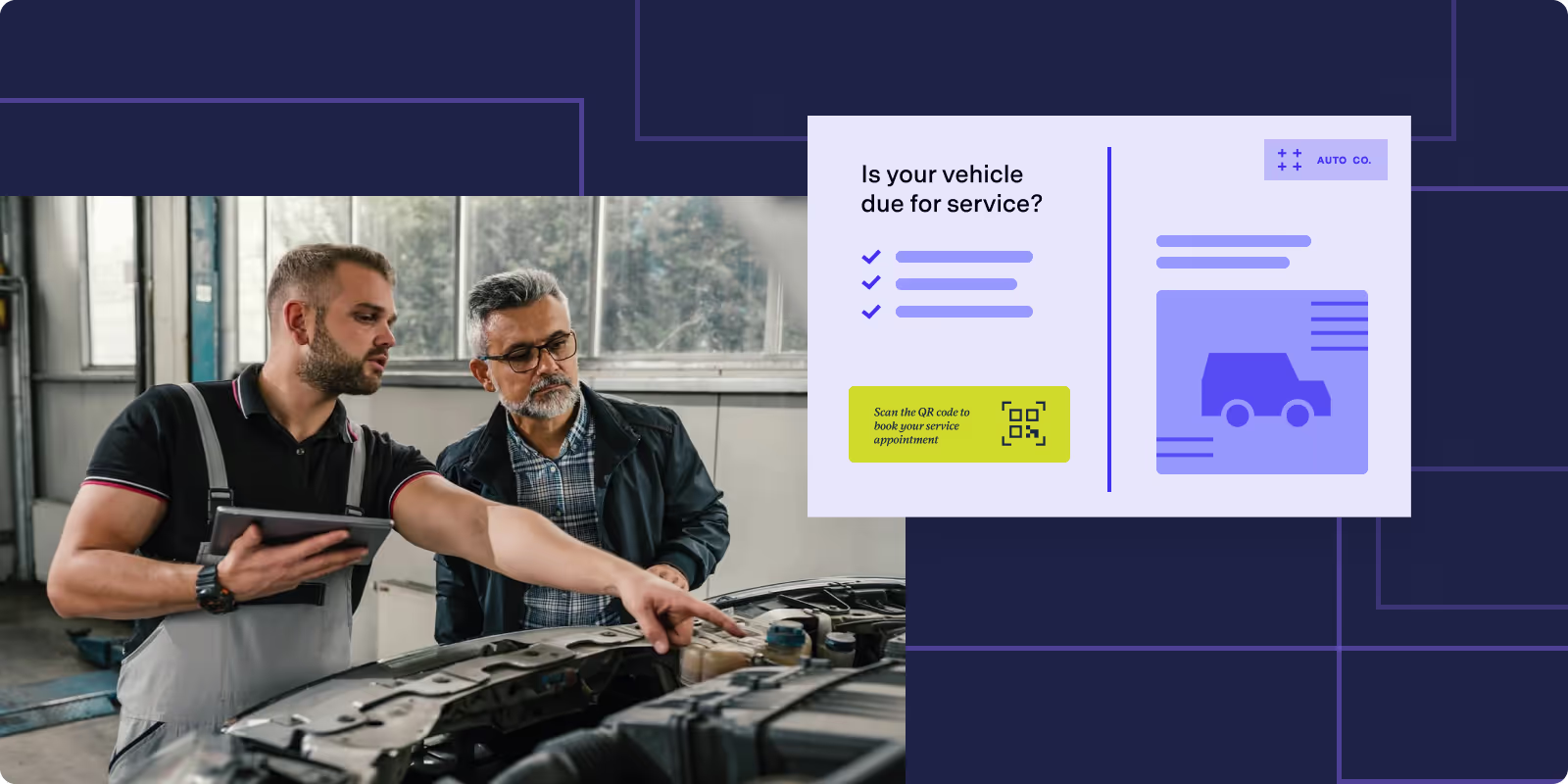
Driving results: the complete guide to automotive direct mail marketing
Complete guide to automotive direct mail marketing for dealerships and repair shops. Achieve 5-9% response rates with targeted campaigns, service reminders, and personalized offers that drive results.

Direct mail automation: how to connect with your marketing tech stack
Automate direct mail campaigns with your marketing tech stack. Connect CRM, marketing automation, and analytics tools to send triggered, personalized mail that increases conversion rates by 28%.

High-Performance Direct Mail Templates: Proven Conversion Designs
Discover high-converting direct mail templates for postcards, brochures, and self-mailers. Learn USPS guidelines, design best practices, and proven conversion techniques to boost your direct mail campaigns.
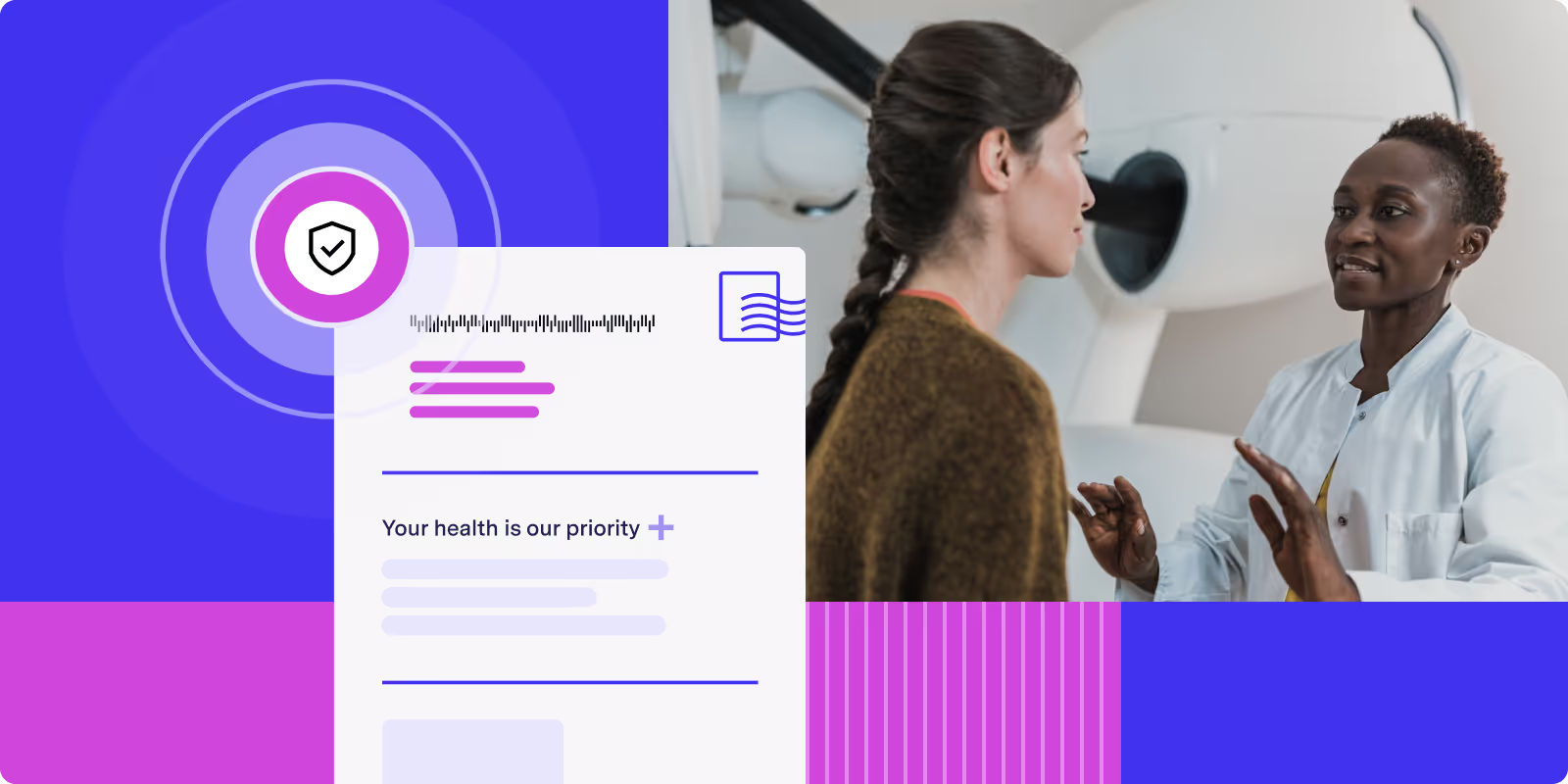
Implementing HIPAA compliant direct mail for healthcare providers
Is there HIPAA-compliant direct mail for healthcare providers? Explore secure mailing protecting PHI and meeting HIPAA standards for patient communication.

Which financial services direct mail options drive the best response?
What are good direct mail options for financial services? Explore letters, postcards, self-mailers and dimensional mailers plus practices that drive response.
.avif)
How to send direct mail automatically from your CRM platform
How do I send direct mail directly from my CRM or platform? Learn how to set up triggers, personalize campaigns, and automate mail sends in minutes.
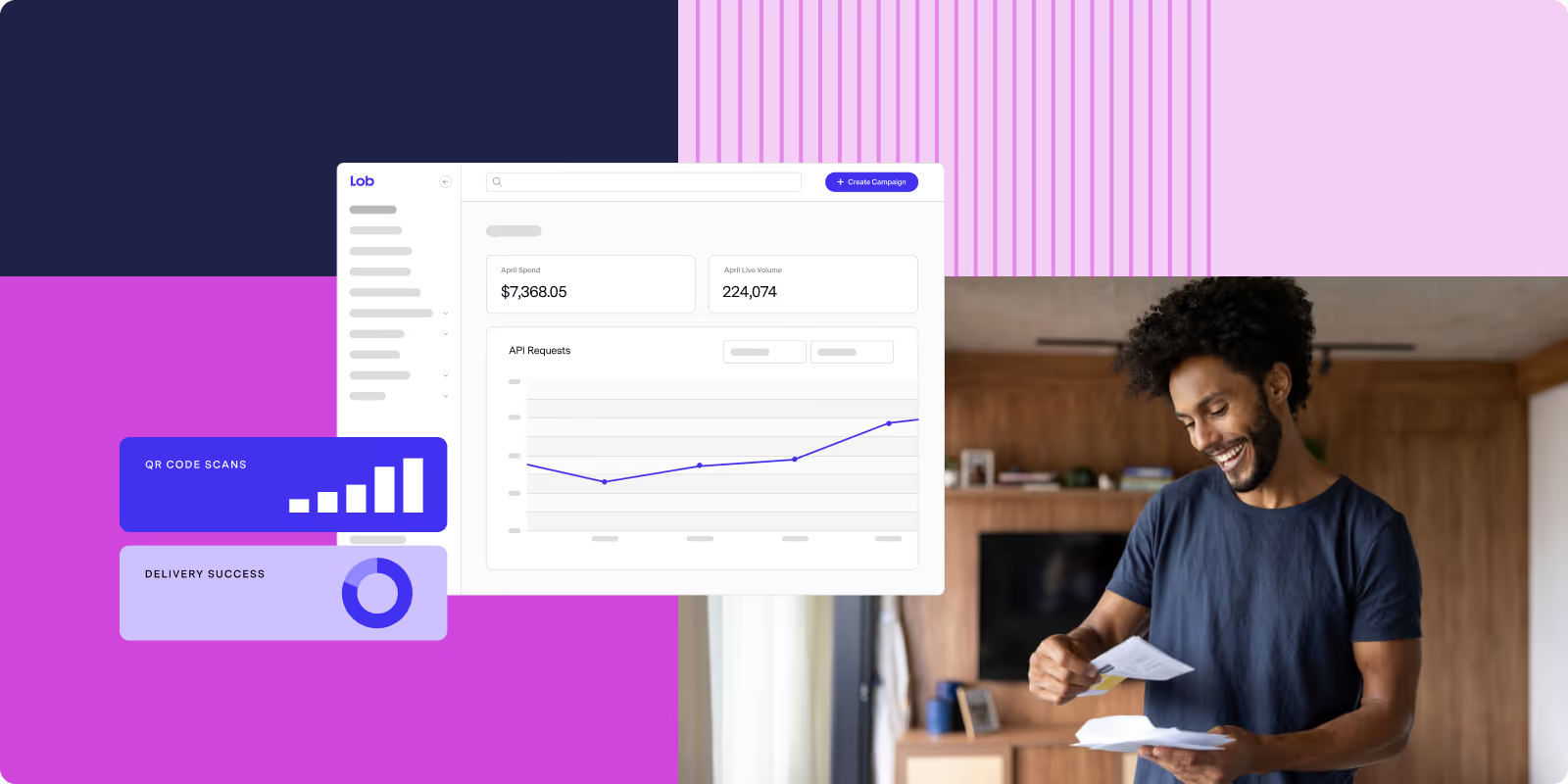
Maximizing customer retention through strategic direct mail
How can direct mail support retention marketing strategies? Explore tactics and personalized mail that drive repeat purchases and boost customer loyalty.

Understanding the difference: Address validation and verification
What’s the difference between address verification and validation: verification confirms it exists and is deliverable; validation checks format accuracy.

Maximizing ROI: Direct mail's essential role in omnichannel marketing
How does direct mail fit into an omnichannel marketing strategy? Physical mail drives engagement, reinforces channels and yields better conversion rates.
Inside Lob's Redesigned Template Gallery
Launch high-performing direct mail campaigns faster with Lob's redesigned Template Gallery. Industry-specific templates built from proven formats that drive results.
What should I look for in a direct mail vendor?
The best direct mail vendors offer end-to-end support – from integration and automation to printing, fulfillment, tracking, and expert guidance.
What’s involved in direct mail printing and fulfillment?
Learn what’s involved in direct mail printing and fulfillment – from file prep and production to addressing, delivery, and tracking.
How can I measure the performance of direct mail campaigns?
Want to know how your direct mail campaigns are performing? Learn how to track delivery, engagement, and ROI using tools like QR codes and analytics.
What are different formats used in direct mail marketing?
Explore the most common direct mail formats – postcards, letters, self-mailers, and booklets – and learn when to use each one to meet your goals.
Personalization at scale: building direct mail campaigns that deliver results
How do I create personalized direct mail campaigns that use customer data to tailor messaging, drive engagement, and track response rates.

Targeted direct mail success: essential best practices for modern marketers
What are best practices for targeted direct mail? Learn to build accurate lists, design eye-catching mailers and personalize offers for higher response rates.

Direct mail and email marketing: when to use each channel
How does direct mail marketing compare to email marketing? Compare engagement, cost, ROI, and timing to pick the right channel.
Choosing a reliable direct mail platform: the complete 2025 guide
What is a reliable direct mail platform for businesses? Discover automated workflows, real-time tracking and data integration for consistent delivery and ROI.
How to calculate your direct mail campaign costs
How do I calculate the cost of a direct mail campaign? Use this simple guide to break down mailing lists, design, printing, postage, and handling expenses.

Inside Lob’s 2025 State of Direct Mail: What today’s consumers really think
Discover what Gen Z and millennials really think about direct mail in Lob’s 2025 Consumer Insights webinar—why they trust it, act on it, and even look forward to it.
How does direct mail marketing compare to email marketing?
How does direct mail marketing compare to email marketing? Explore the strengths of each channel and why the best strategies use both together.
Should I send direct mail before or after my digital campaigns?
Should you send direct mail before or after your digital campaign? Learn how to time your outreach based on lifecycle stage to maximize impact across channels.
Why aren’t customers engaging with my direct mail campaign?
Why isn’t your mail converting? Consumers respond when it’s timely, relevant, and easy to act on. Learn the top reasons campaigns fail and how to fix them.
How can I use direct mail to reach Millennials and Gen Z?
85% of Millennials and Gen Z engage with direct mail – more than any other generation. Here’s how to make your message resonate with younger audiences.
How do I automate direct mail for customer onboarding?
How to automate direct mail for customer onboarding using real-time data, behavioral triggers, and personalized messages without manual campaign management.
What is a physical mail API and how does it work?
What is a physical mail API and how does it work? A physical mail API lets you send letters, postcards, or checks programmatically without file uploads, batching, or print queues.
How can I automate my postcard marketing?
How can I automate my postcard marketing? Direct mail automation platforms connect to your CRM or marketing automation tool to send mail like email.
.png)
Everything you need to know about the USPS First-Class Mail Advertising Promotion
Save 3% on First-Class Mail with USPS’s 2025 promotion. Learn how to qualify by adding a marketing message to mail you’re already sending.
What are the best direct mail solutions for lead generation?
What are the best direct mail solutions for lead generation? It all comes down to smarter targeting, stronger delivery, and a design that makes taking action easy.

Set It and Send It: 3 Automated Direct Mail Workflows for Reactivation
Explore three automated direct mail journeys – from browse abandonment to policy renewals – built to win back customers without adding to your workload.

USPS Integrated Technology promotion: guide to discounts
Learn how to save 3% on postage with the USPS Integrated Technology Promotion. Lob makes it easy to qualify with QR codes, AI, AR, and more—here’s how to get started.

What are the hidden costs of manual mail?
Manual direct mail processes slow you down and increase costs. Discover how to modernize your workflow and scale your direct mail program.

How Lob's Machine Learning Models Aim to Cut Cost and Waste in Direct Mail
Lob tests machine learning models to lower direct mail costs and waste. Discover how data improves postage decisions and flags high-risk addresses.

USPS protests & leadership shakeups: What you should know
USPS protests & leadership changes are underway. Here’s what you need to know to keep your direct mail program running smoothly.

Financial services marketers: Why your credit card mail offers aren't converting (and how to fix them)
Boost response rates with Lob's free templates. Explore helpful templates for pre-approval offers, credit card mail offer templates, & more.
State of Direct Mail 2025 Consumer Insights Edition
Join Lob for a live preview of the State of Direct Mail 2025: Consumer Insights Edition. Get a first look at more unexpected demographic trends.
2025 State of Direct Mail
Join experts from Lob and Comperemedia as they reveal what marketing pros think about direct mail trends, budgets, and bottom lines.

2024 State of Direct Mail Consumer Insights
Join us for a sneak peek at the 2024 State of Direct Mail Consumer Insights study. Learn key trends from 2,000 US consumers in this exclusive 45-minute webinar.

USPS and Lob: Getting Ahead of Direct Mail Technology Trends
USPS and Lob joined forces to discuss how marketers can leverage technology to enhance their direct mail marketing efforts.

Latest from Lob: Trifolds, Legal Letters, and Snap Packs
Watch this webinar to learn how Lob's newest direct mail formats can work for you.

The 2024 State of Direct Mail Marketing
Watch the webinar to get a real-time pulse check from marketers about the current state of direct mail and its role in driving results.

Data-Driven Direct Mail: Personalization Best Practices
Watch the recorded webcast to learn how to use a direct mail automation platform to increase conversion rates with personalized direct mail.
.avif)
2023 State of Direct Mail Consumer Insights
Watch the webinar to hear the newest data on consumers’ usage, preferences, and engagement with direct mail.

Best Practices for More Effective Direct Mail
Watch this demo as we walk step-by-step through the creation of a strategic direct mail campaign.

Optimize Direct Mail for Maximum Results
Watch the webinar to learn how to automate and streamline your direct mail workflows to save time and money, & implement large-scale experiments that drive ROI.

Intelligent Targeting for Direct Mail Campaigns
Learn how to identify, enrich, and reach highly targeted audiences to maximize the effectiveness of your direct mail campaigns with Lob Audience.

2023 The State of Direct Mail
Learn how enterprise marketers use direct mail to drive growth in a changing marketing environment with Lob and Comperemedia's annual State of Direct Mail.

How to Automate Your Nonprofit's Donor Acknowledgement Letters
Watch this session to learn how Lob’s direct mail automation platform saves our nonprofit customers time and money by automating direct mail programs.

Real-Life Direct Mail Strategies to Crush ROI and Budget Goals
Join the experts at Lob to learn how to create a marketing strategy that crushes ROI and budget goals and withstands economic uncertainty.

Drive Retention & Reactivation Success Using Direct Mail
This webinar will give you real-life methods that today’s top marketers use to keep customers engaged, loyal, buying more, and coming back.

Advanced Acquisition Strategies for Intelligent Direct Mail
Learn how to run direct mail acquisition campaigns that drive conversions by combining online and offline marketing channels in our latest webinar.

Breakthrough Strategies for Improving Direct Mail & Out-of-Home ROI
Learn how adding offline channels such as intelligent direct mail and out-of-home advertising to your omnichannel mix drives engagement, leads, and sales.

2022 State of Direct Mail Marketing
Discover key insights into the state of direct mail marketing. Lob and Comperemedia surveyed 150+ U.S. enterprise marketing leaders to reveal modern strategies

The Secret Ingredient to Lightning-Fast, Predictable Direct Mail
Learn how to utilize Lob's APIs to integrate and customize your offline communications with your current systems in our latest webinar.

The Secret Ingredient to Increasing Revenue Throughout the Customer Lifecycle
Boost revenue with Lob’s direct mail insights. Discover how to combine online and offline channels to increase conversions, CLTV, and ROI across touchpoints.

Demo: Direct Mail for the Digital Age
Learn how to utilize Lob's APIs to integrate and customize your offline communications with your current systems in our latest demo.

Demo: Send Physical Mail with Lob for Salesforce Non Profit Cloud (NPSP)
Learn how to drive donor engagement with highly personalized letters and postcards through Lob for Salesforce in our on-demand demo.

Eliminate the Hassle in Claim Processing with Automation
Learn what it costs you in time and money to process and mail checks and how you can increase customer satisfaction with improved payments processing.

Automating the Paper Billing and Collections Process
Learn why paper artifacts are an important part of the accounts receivable process and why automated accounts receivable is valuable and being rapidly adopted.

Salesforce & Lob Integration Demo
Learn how you can take advantage of Lob’s direct mail capabilities and seamlessly integrate it into any business workflow within Salesforce.

Personalization As A Loyalty Game Changer
Learn how brands are leveraging advanced machine learning techniques to enhance the relevance of offers through personalization in our on-demand webinar.
.avif)
Creating A Customer-Focused Loyalty Strategy Based On Data
As we head into 2021, an air tight loyalty strategy rooted in first-party data will be critical for marketing teams that need to hit their number.

Demo: Lob Print and Mail API
Watch direct mail examples of successful companies that execute across digital and direct mail channels with learnings you can apply to your own campaigns.

Predicting the Turn: A Conversation with Dave Knox
Digital transformation has become essential for organizations that want to successfully navigate through uncertainty and stay competitive.

Modernizing Direct Mail Communications: A Fireside Chat With Lob + Oscar Health
Watch Lob discuss how organizations in regulated industries use modern technology to simplify workflows and create strategic advantages that strengthens brand.

Demo: Real Insight Into USPS Delivery Speed Using Lob Analytics
Having sent mail to one out of two households, Lob has a deep understanding of how mail travels through USPS and how recent changes are affecting them.

USPS presents: Direct Mail in an OmniChannel World
USPS reviews their newest initiatives that allow for companies to push the envelope in ways that make direct mail more efficient and insightful.

Lob Address Elements Plugin - Overview and Demo
Learn how to set up front-end address autocomplete and verification for your customer-facing webform easily with our on-demand overview and demo.

The Retention Marketer's Playbook
Learn how marketers across industries can leverage new technologies to increase engagement and LTV.

How To Strategically Implement Direct Mail Automation For Long Term Success
There are four main challenges every business faces when setting up direct mail programs at large scale: resourcing, budget, optimization, and execution.

The Virtual Direct Mail Symposium
Learn how technology is transforming direct mail processes, and allowing organizations to be more responsive while reducing costs in our on-demand symposium.

Direct Mail’s Digital Transformation: A Fireside Chat with Lob + Verizon
Learn how enterprise organizations use modern technology to simplify workflows and create strategic advantages that drive real business results.

Live Demo: Financial Services Embrace APIs to Enhance their Direct Mail
Technology has transformed direct mail, allowing for FinServ organizations to send timely, relevant mail that saves time, processing, and verification costs.

Reimagining Customer Communications in Insurance with CPH, VillageCare, & Oscar Health
Learn how insurance leaders transformed their customer engagement and outreach offline by leveraging modern technology to coordinate across multiple channels.

Strategic Retention Marketing with Direct Mail Automation in Salesforce Marketing Cloud
Learn how organizations use Lob to boost engagement throughout the customer lifecycle, with intelligent direct mail in our on-demand webinar.

3 Companies Automating Offline Communications To Increase Efficiency & Compliance
Learn how these organizations are using automated direct mail to save on operational costs and compliance with triggered mail and detailed tracking analytics

How Insurers Can Improve Engagement & Ensure Compliance With Modern Direct Mail
Learn how modern insurers are embracing intelligent direct mail to transform their physical mail to fully automate, personalize, and trigger mail.

Live Demo: How Retailers Can Leverage Offline Marketing for Online Retention
Learn how to automate direct mail campaigns from within your marketing automation or CRM tools in our on-demand webinar.

Winning Multichannel Marketing: Strategic Offline Engagement for Modern Retention
Learn how to integrate Lob’s direct mail automation into Blueshift’s data activation platform, and get the most out of your omnichannel marketing campaigns.

Embracing Digital Transformation: Financial Services Empower Offline Operations With Lob
Learn how to increase the scalability, reliability, and flexibility of your direct mail efforts and mitigate the risks of sending direct mail in our webinar.

Why Direct Mail is an Engagement Game Changer
Learn how you can effectively leverage direct mail throughout your customer journeys and innovative direct mail use cases across the customer lifecycle.

FinTech Reduces Fraud and Optimizes Resources with Lob Address Verification API
Use Address Verification API to identify fraudulent activity to reduce erroneous entries in your KYC solution and eliminate costly undeliverable mail.

Lob Address Verification Demo Webinar
Learn how you can integrate Lob Address Verification API in minutes to reduce bad address data by 97% and stop sending mail to an undeliverable addresses.

Lob Address Verification Platform Webinar
Learn how you can integrate Lob Address Verification API in minutes to reduce bad address data by 97% and stop sending mail to an undeliverable addresses.

Improve your Ecommerce Experience with Data and Personalization
Learn how to create a memorable eCommerce customer experience through personalization and enhancing customer data to streamline delivery and reduce costs.

The State of Direct Mail
Direct mail has long been utilized by marketers. While this proves its importance, it fails to give insight on what strategy marketers are utilizing.

Product Video: Lob Address Verification
Reduce bad addresses by 97% so you don’t waste another dime on undeliverable mail, watch our demo video and start verifying addresses in minutes.

5 Companies Doing Direct Mail Right
High-performing direct mail leverages design, personalization, messaging and more to catch the eye of the reader. Here are 5 examples of effective print and mai

4 Ways To Prevent Revenue Loss
Learn how world-class operations teams use technology to recover lost revenue through customer centric collections strategies and prevent future revenue loss.

Data-Driven Direct Mail
Whether it’s for retargeting, retention, or re-engagement, these direct mail best practices can supercharge campaigns across the customer lifecycle.
2026 State of Direct Mail
Join experts from Lob and Comperemedia as they reveal what marketing pros think about direct mail trends, budgets, and bottom lines.

The Direct Mail Marketing Cheat Sheet
Master direct mail marketing effortlessly with Lob’s cheat sheet. Discover advanced audience targeting, automation, personalization, and analytics strategies. Learn more!

5 Things Lob Can Do for Your Direct Mail
The future of direct mail is automation and enterprise brands are ditching legacy workflows for better, more efficient ways of executing direct mail that drive greater response and ROI, can be triggered based on customer behavior, tracked, and are carbon-neutral.

Direct Mail Secret Sauce: Dos and Don'ts
Lob shares the secret sauce to direct mail marketing with dos and don’ts to make your direct mail as effective as possible to drive more customer lifetime value.

Lobcast Podcast: Marketing AI & Appletinis
We're talking about all things marketing AI on today's Lobcast Podcast! Special guest Pini Yakuel from Optimove joins us to chat about AI in marketing.

Lobcast Podcast: Deconstructing Direct Mail & Dessert Manhattans
We're doing things differently today on the Lobcast Podcast and deconstructing what's working in some real-life direct mail campaigns. Watch now!

Lobcast Podcast: State of Direct Mail Consumer Insights & Island Cosmos
In this podcast, hear the findings from our 2023 State of Direct Mail Consumer Insights report to uncover consumers’ perspectives on direct mail.

Lobcast Podcast: A/B Testing & Apricot Bellinis
Testing, testing! Come learn all about A/B testing in marketing campaigns, especially in direct mail, on this episode of the Lobcast Podcast. Listen now!

Lobcast Podcast: Marketing ROI & Mai Tais
Let’s break down marketing ROI and talk about how direct mail can be a great channel for improving ROI and lifting the results of other marketing channels.

Lobcast Podcast: Marketing Optimizations & Old Fashioneds
Optimization is a journey, not a destination. On this podcast episode, we’re digging into the principles behind continuous marketing optimizations.

Lobcast Podcast: Personalization & Pina Coladas
On this episode of the Lobcast Podcast, we're talking best practices for personalization in marketing, whether it's direct mail or digital marketing.

Lobcast Podcast: Operational Mail & Orange Margaritas
Mix up an orange margarita and listen in as we talk about automating and optimizing operational mail on the Lobcast Podcast. Guest speaker is Dave Krawczuk

Lobcast Podcast: Marketing Metrics & Margaritas
We’re mixing up some margaritas and talking all things marketing metrics, both digital and direct mail, on the Lobcast Podcast. Listen to the episode now!

Lobcast Podcast: Marketing Data & Million Dollar Cocktails
Listen to episode 12 of the Lobcast Podcast to learn how to use marketing data and lists to improve your marketing campaigns and drive better ROI.

Lobcast Podcast: Spring Marketing Strategies & Strawberry Mimosas
It's springtime and it's time to spring into action when it comes to tidying up spring marketing campaigns. Learn more on this Lobcast Podcast episode.

Lobcast Podcast: Spring Cleaning Marketing Workflows & Whiskey Sours
Mix up a whiskey sour and listen to this episode of the Lobcast Podcast where we're talking all things marketing operations and spring cleaning workflows.

Lobcast Podcast: Intelligent Mail & Iced Mochatinis
Learn how to harness the power of intelligent mail in your marketing strategy to drive better ROI on this episode of the Lobcast Podcast.

Lobcast Podcast: 2023 State of Direct Mail & Spritzes
Get the latest facts and findings when it comes to how marketers are using direct mail as we talk about the 2023 State of Direct Mail on the Lobcast.

Lobcast Podcast: Slide Into a New DM - Direct Mail & Daiquiris
Listen to episode 7 of the Lobcast Podcast where we share how marketers can slide into a new DM: Direct Mail! Hear about best practices and how to start!

Lobcast Podcast: Timeless Tactics & Tequila Sunrises
Mix up a tequila sunrise and listen in to episode 6 of the Lobcast Podcast as we talk about timeless marketing tactics to add to your 2023 strategy.

Lobcast Podcast: Marketing Resolutions & Raspberry Mocktails
Mix up a mocktail and listen in to episode 5 of the Lobcast Podcast as we talk 2023 marketing trends and marketing resolutions.

Lobcast Podcast: Budgets & Beermosas
Mix up a beermosa and listen in to episode 4 of the Lobcast Podcast to hear our chat about direct mail budgets and how direct mail fits in marketing.

Lobcast Podcast: Marketing Mail & Mulled Wine
Listen in as we talk about all things marketing mail, both email and direct mail, on episode 3 of the Lobcast Podcast: Mixers and Marketing!

Lobcast Podcast: State of Direct Mail Consumer Insights & Irish Coffee
Listen in as we talk about the 2022 State of Direct Mail Consumer Insights and key findings marketers need to know about direct mail marketing.

Lobcast Podcast: State of Direct Mail & Dark and Stormy
Mix up a dark and stormy and hear how marketers are leveraging direct mail in their marketing on episode 1 of the Lobcast Podcast: Mixers and Marketing!

Meet the Mailers: Driving ROI with Direct Mail Automation
Paul Bobnak at Who's Mailing What! interviews Lob's own Summer Hahnlen about how driving ROI through personalized direct mail.

Direct Mail Marketing Master Class
From direct mail newbie to seasoned professional, Lob's Direct Mail Marketing Master Class has something for everyone. Discover the latest trends and stats, learn how to optimize your campaigns, reveal how-to's to help you execute your direct mail more efficiency and effectively.
